ACL- Access Control List with is used to control unauthenticated access with help of a list. Normally applied on routers.
Timed Based ACL- ACL which work on a particular time like I am a network admin in a company and company doesn't provide internet access on weekends or after office hours then timed access list is used.
so we can say that "Timed based ACL permit/Deny traffic for a time/day period"
Example---
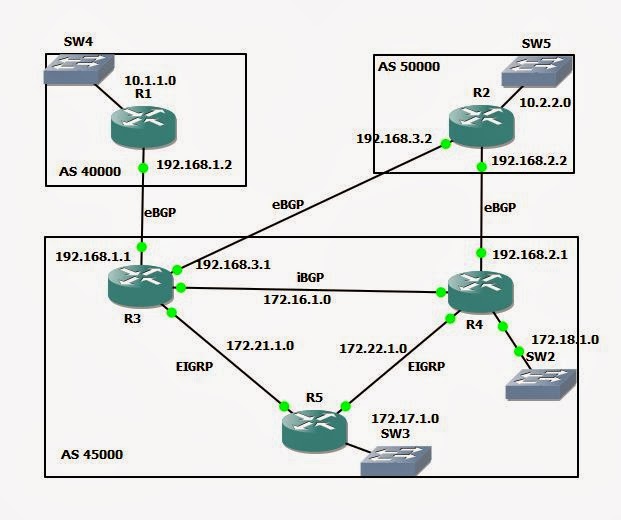
Here I have a simplest topology 3 router R1, R2 and R3.But R3 is working as a PC and R2 is working as destination.On R2 we will apply ACL.I will use ACL to permit ping for a time period.
1. Connect all routers and give ip to interfaces.
2.We want R3 to work as a pc so
R3(config)#no ip routing
3.Time to create ACL but first first we have to create timed access list.No we have two option
(i).Absolute-- For a particular time period "<start time date> <end time date>"
(ii)Periodic---For a day period "<day-of -the-week> hh:mm to <day-of-the-week> hh:mm"
While we using periodic we have multiple option-
A) daily- Mon to Sun
B)Weekend-Sat and Sun
C)Weekday-Mon to Fri
4.Now create a extended ACL and apply it on interface.
R1(config)#time-range permit-ping
absolute start 13:00 26 Nov 2013 end 14:26 Nov 2013
R1(config)#access-list 120 permit icmp any any time-range permit-ping
R1(config)#int f 0/0
ip access-group 120 in
After applying this ACL I am able to ping R2 from R3 from 1:00 PM to 2:00 PM on 26 Nov 2013.
"Note- you can see currant status of ACL by show acces-list"
Timed Based ACL- ACL which work on a particular time like I am a network admin in a company and company doesn't provide internet access on weekends or after office hours then timed access list is used.
so we can say that "Timed based ACL permit/Deny traffic for a time/day period"
Example---
Here I have a simplest topology 3 router R1, R2 and R3.But R3 is working as a PC and R2 is working as destination.On R2 we will apply ACL.I will use ACL to permit ping for a time period.
1. Connect all routers and give ip to interfaces.
2.We want R3 to work as a pc so
R3(config)#no ip routing
3.Time to create ACL but first first we have to create timed access list.No we have two option
(i).Absolute-- For a particular time period "<start time date> <end time date>"
(ii)Periodic---For a day period "<day-of -the-week> hh:mm to <day-of-the-week> hh:mm"
While we using periodic we have multiple option-
A) daily- Mon to Sun
B)Weekend-Sat and Sun
C)Weekday-Mon to Fri
4.Now create a extended ACL and apply it on interface.
R1(config)#time-range permit-ping
absolute start 13:00 26 Nov 2013 end 14:26 Nov 2013
R1(config)#access-list 120 permit icmp any any time-range permit-ping
R1(config)#int f 0/0
ip access-group 120 in
After applying this ACL I am able to ping R2 from R3 from 1:00 PM to 2:00 PM on 26 Nov 2013.
"Note- you can see currant status of ACL by show acces-list"